Good evening and welcome to my evening post for today I will explain what Hash function.
What is a Hash?
A hash is a cryptographic function that have the ability to convert data input into a unique alphanumeric characters, which are unrepeatable. Hash can be describe as a Cryptographic function use in securing the integrity of data. A hash function is a computational tool which converts an input into a compressed output. The input are of arbitrary length while its output have a fixed length. We can say that it's a tool that is use to represent a larger data into a smaller data. It is a one-way function and is therefore practically impossible to invert or reverse its computation.
In a Blockchain, a Hash function is use to validate the integrity and authentication of various data and also use to generate wallet addresses. You can also say that a Hash is a one-way function which scrambles text to generate a unique code. It also help to convert large transaction data into a small data, it is a very useful function in the Blockchain, where it generate all the large transaction data into a hash function. Since a hash is use to compress data, there is a possibility that there might be some collisions and these is where Collision Resistance comes in. Hash function has these main fundamental properties:- Collision Resistance, Preimage Resistance and Second Preimage Resistance.
What is Resistance to Collision?
Resistance to Collision is one of the fundamental properties of hash function, and It is designed to resist any form of collision, that is to say that two different inputs will never collide, it must generate different output. Resistance to Collision in simple term, is that a collision attack is very difficult if not near impossible. it is mathematically impossible to find two different inputs having same output.
Like for example, a and b can not generate h(a) = h(b). When we say that a hash is collision resistant is when it has be proven that the hash two inputs are not producing same output. A hash function can only be seen as collision resistance, if it output contains 160bit length minimum.
What is Resistance to preimage?
Resistance to Preimage is one of the fundamental hash function properties and is a one way function, it is almost impossible to invert. That is to say that an element in the range of a hash function, it will be computationally impossible to find input that will maps that element. Resistance to Preimage is a one-way straight forward, that is used for functions that have input and output of same size, just One-Way no reverse.
For a hash function to be Resistance to Preimage, it output must have 90 bits minimum. When a hash function (h) produced a hash with z value, it will be difficult, if not impossible to find any input value (x) that hashes to z. This is why it is difficult for an attacker with a hash value and have the intention of discovering the input value.
Tronscan hash last block and the latest transaction verifying.
To view the last block hash and latest transaction hash, you have to visit Tronscan at https://tronscan.org.
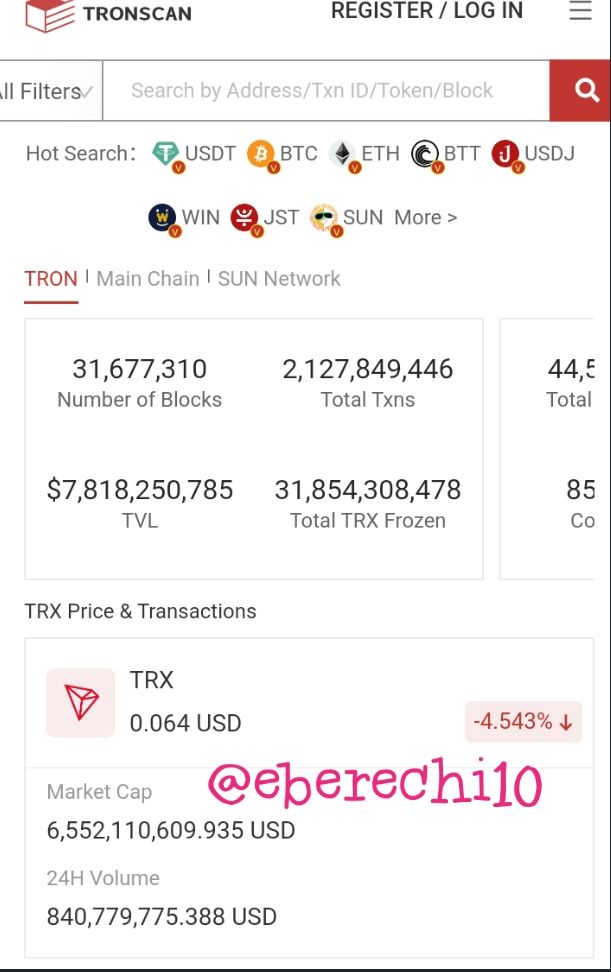
Now roll down to view block lists and click on the last block
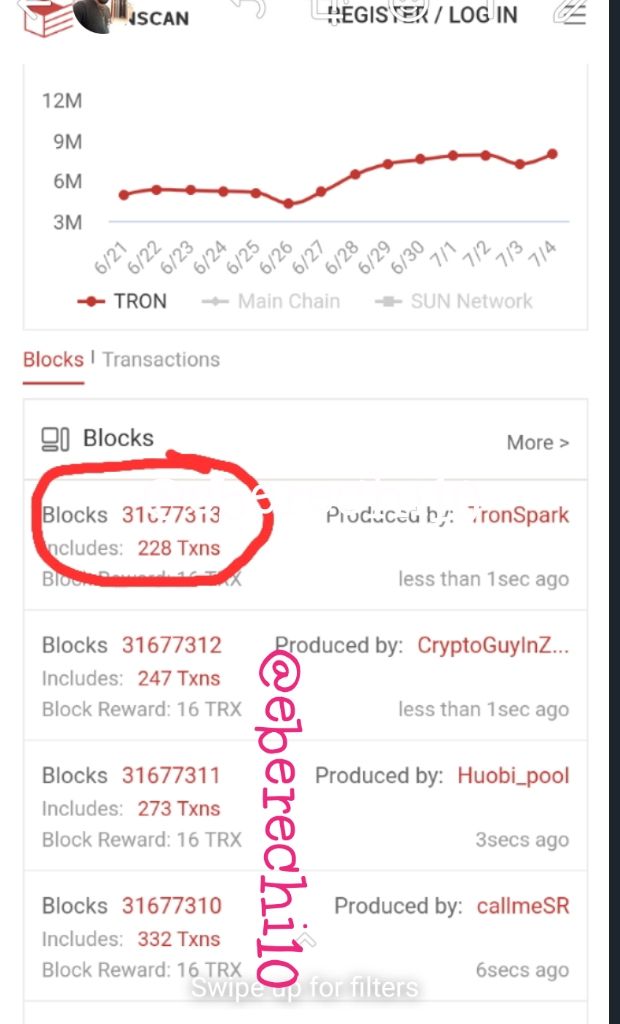
Click on the last block on the lists of blocks here the last block is number 31677313
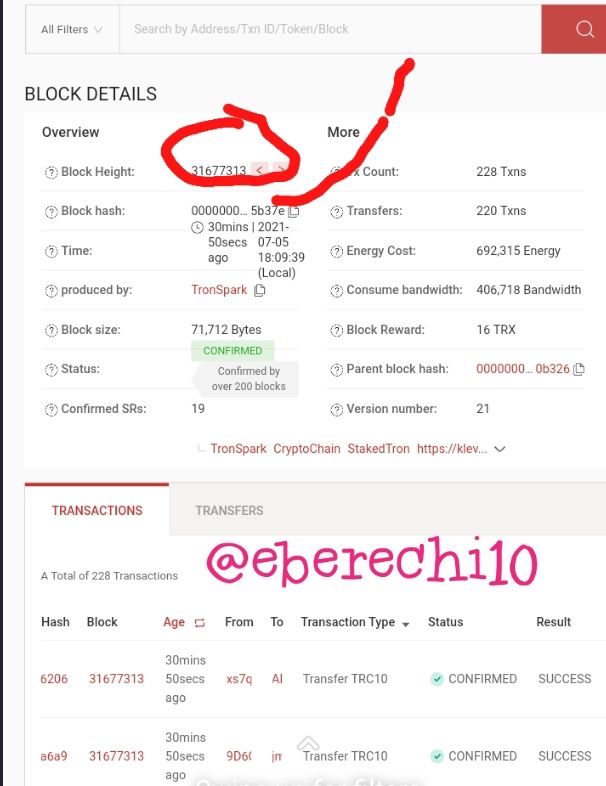
It will display the block details, here the block hash is 0000000001e35b816345b6d518f69b0ee251bb65cc2261fddf6b6ef82c55b37e
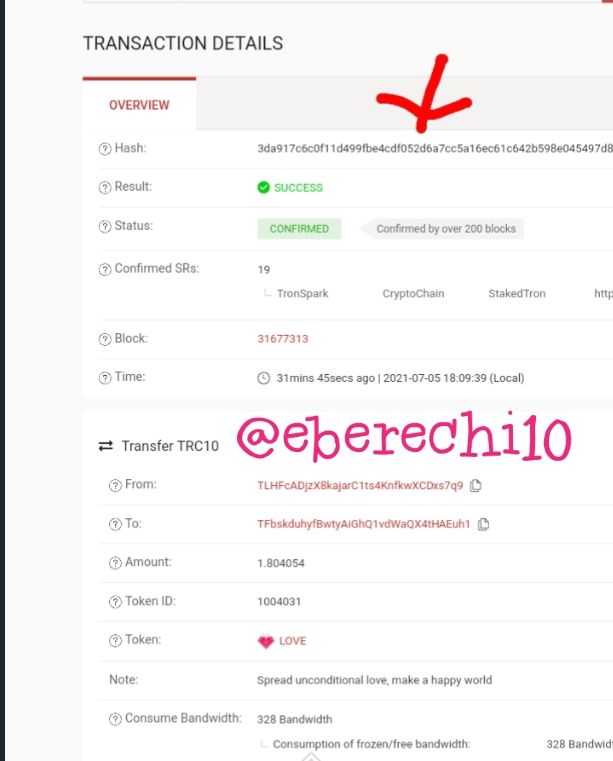
Now click on the last transaction on the list of transaction to view the transaction details. The latest transaction hash 3da917c6c0f11d499fbe4cdf052d6a7cc5a16ec61c642b598e045497d8662065
The Etherscan last block hash and transaction verifying.
To verify etherscan last block hash and latest transaction hash, you have to visit https://etherscan.io and roll down, to see the last block.
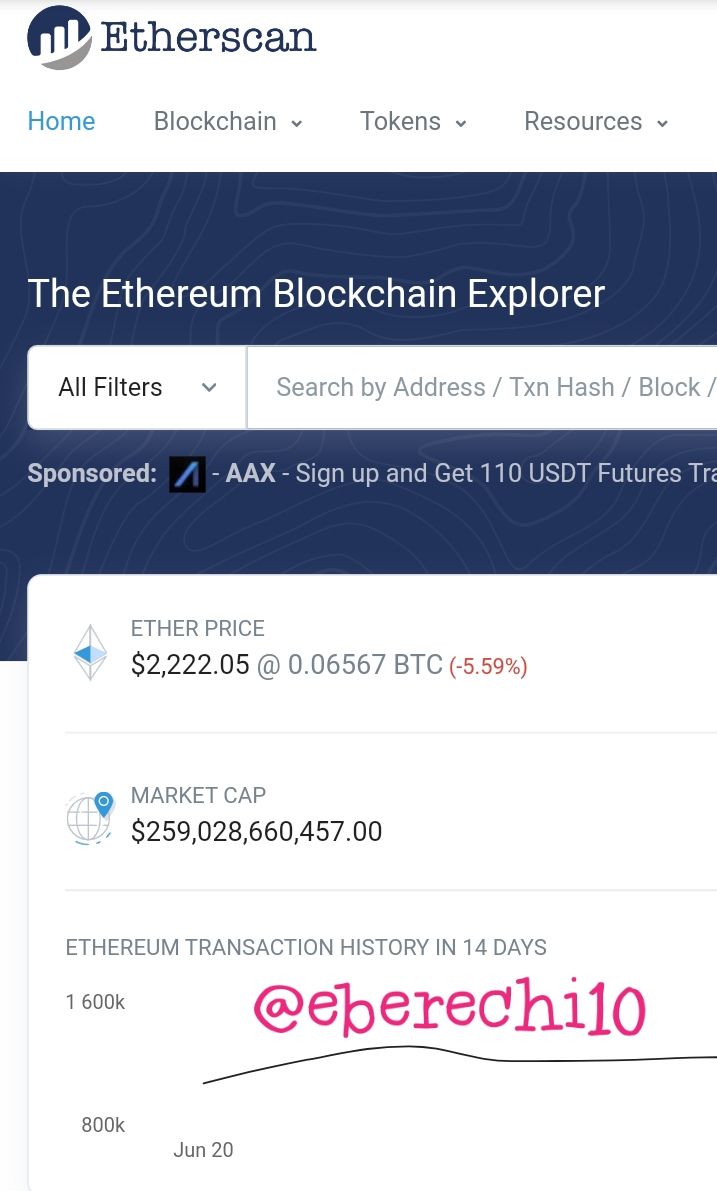
The last block on etherscan is block number 12769055.
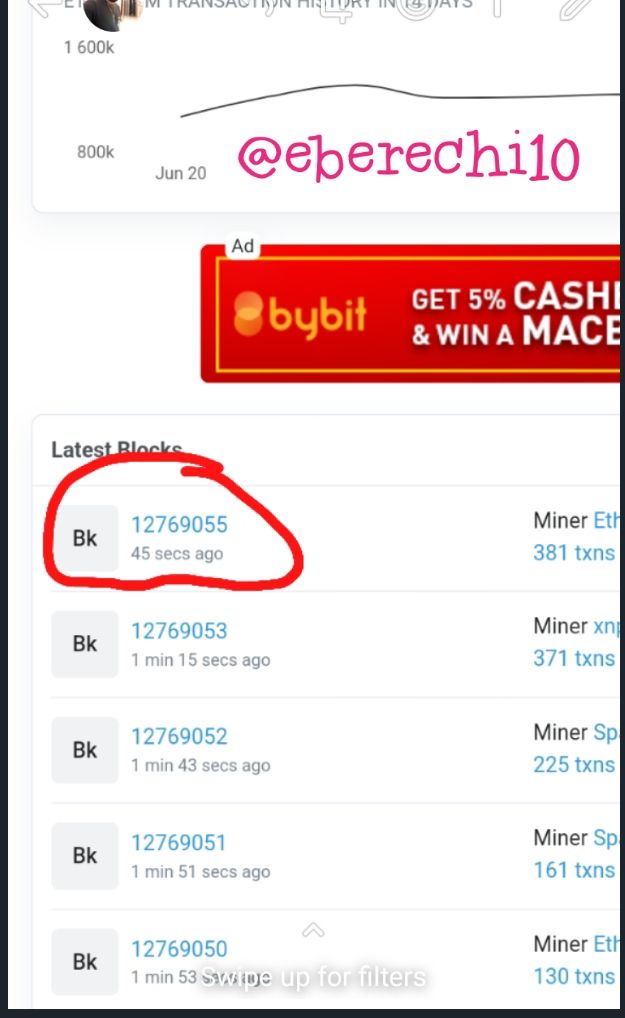
Now click on the block to display the block details.
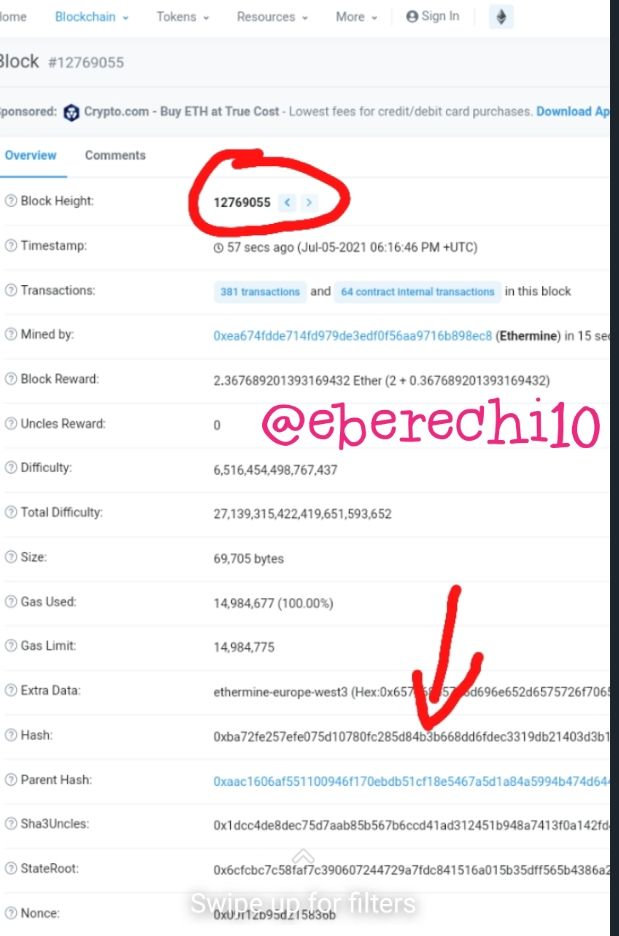
Now the block details have been displayed, the block hash is
0xba72fe257efe075d10780fc285d84b3b668dd6fdec3319db21403d3b14bae211.
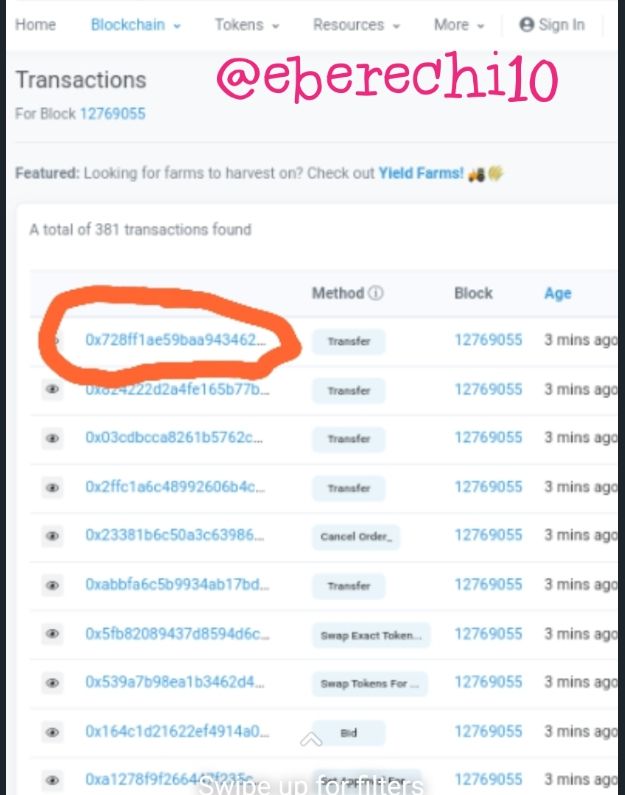
Now click on transaction to view the latest transaction details
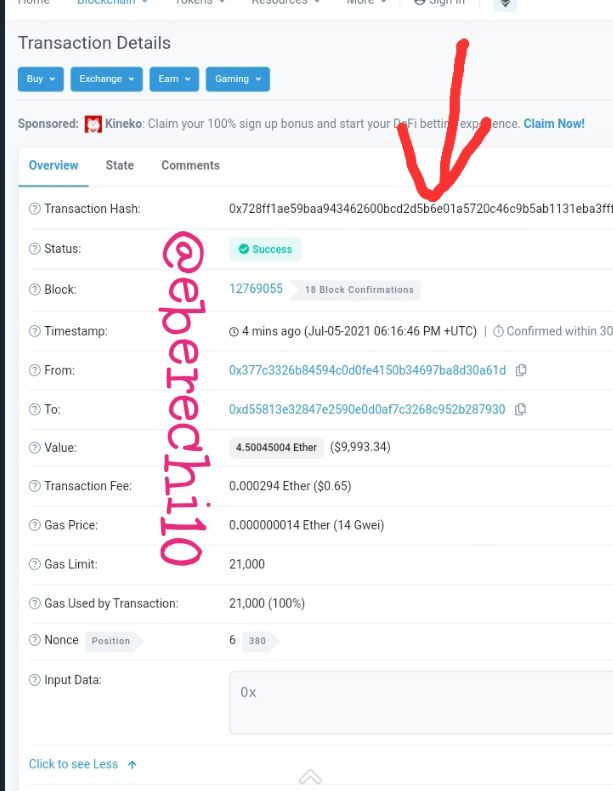
The transaction details have been displayed, with a transaction hash 0x728ff1ae59baa943462600bcd2d5b6e01a5720c46c9b5ab1131eba3fffdfc829
Generate hash using SHA-256, with CryptoAcademy and cryptoacademy. Explain the difference.
An online password generator was used to generate the hash function of these two words using SHA256. https://passwordsgenerator.net/sha256-hash-generator/, CryptoAcademy and cryptoacademy.
CryptoAcademy
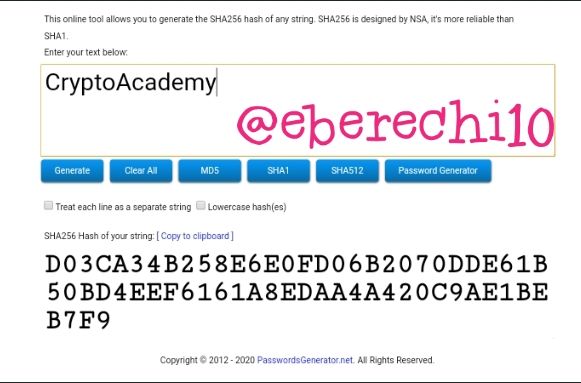
CryptoAcademy generated this hash function
D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9
CryptoAcademy
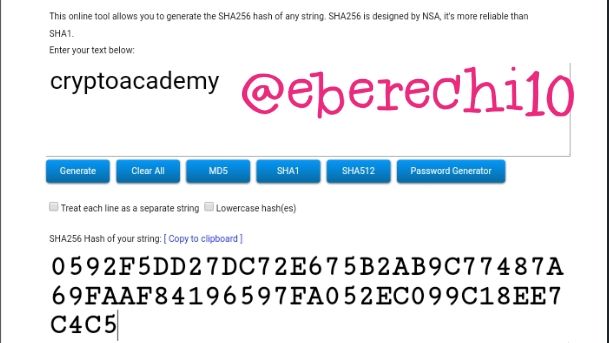
cryptoacademy generated this hash function
0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
Explain why the two words has different hash functions.
It's clearly visible from the screenshots above that two inputs that don't have same content will generate entirely two different outputs The two inputs has different hash outputs because SHA-256 is resistance to collision as explained above, this makes it impossible for the output to collide, so therefore it will be computationally impossible and impracticable to generate a collision.
Though they are similar but are not the same content, and hash function are designed that two inputs can't generate same hash output because of resistance collision. So therefore CryptoAcademy and cryptoacademy can't generate same hash function. XX is not = xx.
Difference between hash and cryptography.
Hash
Foreordained, which simply means that same message will always have the same hash.
Irreversible: You cant generate a message that yielded the hash value.
Unique: You cant find two different inputs that generate same hash output.
Any adjustment to the input will heavily alter the hash output, which is called the avalanche effect.
All hash function are not cryptography.
Hash help to identify data tampering after it's have been signed and also in identity verification.
Cryptography
- All cryptography is a hash function.
Cryptography provide security to data.
Cryptography ensure confidentiality, by making sure that the information are encrypted.
It ensure that the data are not altered in storage or when transit between the sender and the receiver.
It also help to authenticate the sender and the receiver, by confirming each other's identity and location.
Conclusion
A hash function today is one of the fundamental tools use in Blockchain and it is also of great importance to the cryptocurrency industry. It's use to generate wallet addresses, authentication and validation of transaction etc. A hash must be resistance to collision, this will ensure that it's impossible for two different inputs to generate same output hash. Resistance to preimage and collision are the main fundamental three properties a of hash. If a hash is resistance to collision, then that hash is also resistance to second Preimage