SSH stands for Secure Shell.
It is a network protocol that allows secure, encrypted communication and data transfer between two devices over an insecure network.
SSH is widely used for accessing remote servers, logging into a server, and executing commands securely.
Key aspects of SSH
- Secure Communication: SSH provides a secure way to connect to a remote server over an unsecured network, such as the internet. It ensures the confidentiality and integrity of the transmitted data by encrypting the connection.
- Authentication and Encryption: SSH uses encryption algorithms to secure the data during transmission. It employs various methods for user authentication, including password-based authentication, key-based authentication, or two-factor authentication.
- Remote Access and Control: SSH allows users to remotely log in to a server or device and execute commands as if they were physically present at the machine. It's commonly used by system administrators, developers, and users to manage and access servers securely.
- File Transfer: Apart from remote command-line access, SSH protocols are used for secure file transfer. Tools like SCP (Secure Copy Protocol) or SFTP (SSH File Transfer Protocol) enable the secure transfer of files between local and remote systems.
- Portability and Flexibility: SSH is a cross-platform protocol, available on most operating systems, such as Windows, macOS, and various distributions of Linux.
SSH involves a client-server architecture where the client initiates a connection to the server. Users require SSH client software to connect to a remote server that has an SSH server application running.
Main Components
SSH works through two main components.
- SSH Client: The client is used by the person initiating the connection to the remote server.
- SSH Server: The server is installed on the machine being accessed and manages the incoming SSH connections.
SSH keys play a vital role in SSH authentication, providing a more secure and convenient method compared to password-based authentication.
Keys are used to authenticate the client to the server without needing to transmit a password during each connection.
SSH is a fundamental tool for secure access and communication, especially in the realm of system administration, network security, and remote server management.
Generate SSH Key
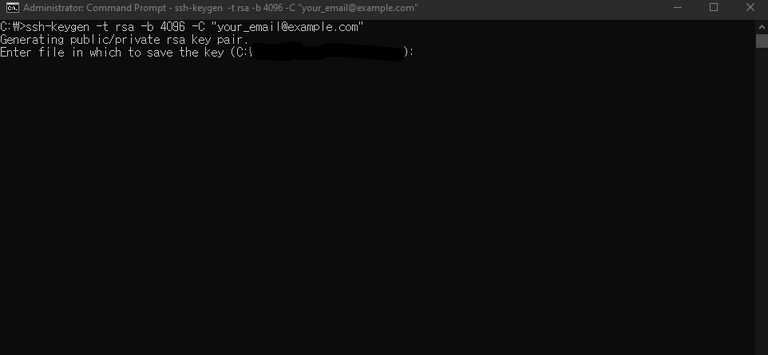
If you haven't generated an SSH key on your local machine, you can do so using the following command in your terminal or command prompt:
ssh-keygen -t rsa -b 4096 -C "[email protected]"
Replace "[email protected]" with the email associated with your GitHub account.
This command generates a new SSH key using the provided email and the default location.