Have you ever wanted to uncover hidden messages that only a select few can decipher? Do you find yourself fascinated by the intricacies of cryptography, the art and science of creating secure communication? Look no further than this blog post, where we will delve into the world of cryptography, explore its history and modern-day applications, all while learning how to decode hidden messages like a pro. So grab your decoder ring and get ready to unlock some secrets!
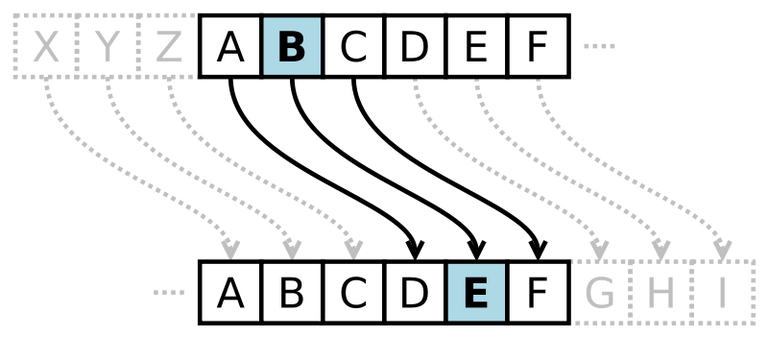
Cryptography is the practice of secure communication in the presence of third parties. Cryptography can be used for a variety of purposes, including protecting information from unauthorized access, sending secret messages, and preventing fraud.
Cryptography is based on mathematical principles and uses various techniques to encode and decode data. The most common cryptographic algorithms are symmetric-key algorithms, which use the same key to encrypt and decrypt data. Asymmetric-key algorithms use two different keys, one to encrypt data and one to decrypt it.
Cryptography is used in a wide range of applications, including online banking, email security, and secure communications between businesses. Cryptographers continue to develop new methods of cryptography that are able to protect information from increasingly sophisticated attacks.
How does cryptography work?
Cryptography is the practice of secure communication in the presence of third parties. It is a method for protecting information by encoding it into a form that is unreadable to anyone but the intended recipient. Cryptography can be used to protect personal information, financial data, and secret messages.
Cryptographic algorithms use mathematical functions to create an encrypted message. The algorithm generates a random number and uses that number to encrypt the message using an encryption key. The encryption key is also used to decrypt the message. Anybody who knows the encryption key can decrypt the message.
The security of cryptography depends on two things: the secrecy of the encryption key and the strength of the cryptographic algorithm. Cryptographers often use combinations of different algorithms to create stronger messages.
Cryptography history
Cryptography is the practice of secure communication in the presence of third parties. Cryptography history dates back to ancient Babylonian times, when ciphers were first developed. In the Middle Ages, cryptography was used to encrypt and decrypt messages. During the Renaissance, cryptography was used to protect trade secrets and conceal political messages. Modern cryptography began in the early 19th century with the development of codebreaking techniques by mathematicians such as Charles Babbage and Alfred Vail. Since then, cryptography has evolved into a field that is used for a wide variety of purposes, including online security, authentication, and data integrity.
Modern cryptography
Cryptography is the practice of secure communication in the presence of third parties. Cryptography has been used throughout history for a variety of purposes, including military, diplomatic, and commercial secrecy. Today, cryptography is used to protect information from unauthorized access and disclosure.
Cryptography is based on symmetric-key cryptography, which uses the same key to encrypt and decrypt data. Symmetric-key cryptography is generally more secure than asymmetric-key cryptography because it requires two separate keys—one to encrypt data and one to decrypt it. Asymmetric-key cryptography relies on a single key to encrypt and decrypt data.
One common type of asymmetric-key cryptography is digital signatures. A digital signature uses a private key to generate an electronic signature that can be verified by anyone who knows the public key. The advantage of digital signatures is that they provide proof that the sender authorized the transmission of the message.
Another common type of asymmetric-key cryptography is encryption using a shared secret key. When users share a secret key, they are able to encrypt data using the shared key without having to exchange any passwords or other confidential information. Shared-secret encryption is often used in conjunction with authentication systems, such as mutual authentication cookies or smart cards.
Many modern cryptosystems use several layers of security, including:
Cryptography tools and techniques
Cryptography tools and techniques are essential for protecting data from unauthorized access. Cryptographic algorithms are used to encode and decode data in a secure manner. Cryptanalysis is the process of attacking cryptography systems in order to decrypt the data. There are many different cryptographic algorithms, each with its own strengths and weaknesses.
One common type of cryptography is symmetric-key cryptography. In this system, the same key is used to encrypt and decrypt data. Symmetric-key cryptography is relatively easy to fool because an attacker cannot use the same key to both encrypt and decrypt data. To protect against this type of attack, symmetric-key cryptography typically uses a shared secret key between the sender and recipient.
Another common type of cryptography is asymmetric-key cryptography. In this system, two different keys are used to encrypt and decrypt data. Asymmetric-key cryptography is more difficult to fool because an attacker cannot use the same key to both encrypt and decrypt data. To protect against this type of attack, asymmetric-key cryptography typically uses a public key and a private key.
Cryptographic algorithms can also be used to create digital signatures. A digital signature is a mathematical algorithm that allows you to verify the authenticity of a message or file by using your private key. A digital signature can be used to prove that you are who you say you are or that someone else sent you the message or file you claim to have received.
Conclusion
Cryptography is an art and a science, and it's an essential tool for both protecting information and enabling secure communications. In this article, we've explored the history of cryptography, discussed the different types of encryption, and provided tips on how to decode hidden messages. Hopefully this information has given you a better understanding of cryptography - both its artistry and its underlying principles. If you have any questions or would like help implementing cryptographic techniques in your own life, please don't hesitate to reach out!
Re🆔eD

🤬
Curated by @ultravioletmag