After conducting an investigation into the recent $160 million exploit of Wintermute in Ethereum chain, digital assets firm Amber Group said it was able to repeat the full attack vector.
Amber recalculated the private key of the address that market-making firm Wintermute had used.
In its analysis of the hack, it took the firm only two days (48 hours) to crack the private key with the help of a MacBook M1 computer.(MacBook M1 with 16G memory)
To do this, the firm launched a brute force attack that extracted the seed phrase for Wintermute's address.
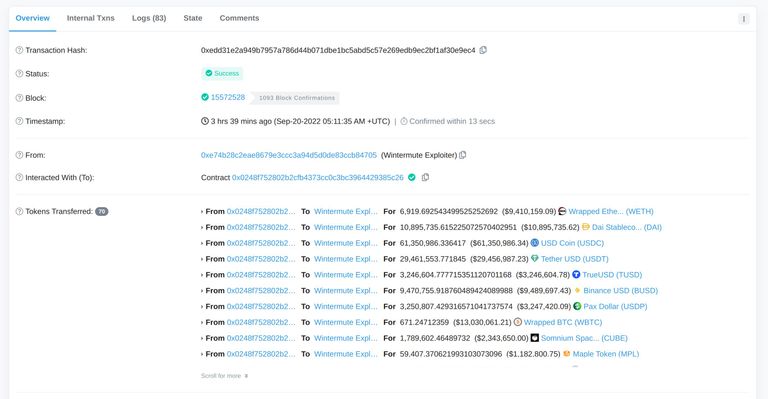
On Sept. 20, crypto market-making firm Wintermute was hacked for $160 million from its Ethereum Vault. The vault relied on an admin address, which was targeted to extract the private key to move the funds.
Wintermute’s hacked admin account was a “vanity address”
That is a type of crypto address containing identifiable names or numbers within them — or which have a particular style — and can be generated using certain online tools including Profanity.
Security analysts at 1inch found that private keys of vanity addresses generated with Profanity could be calculated by malicious hackers to steal funds.
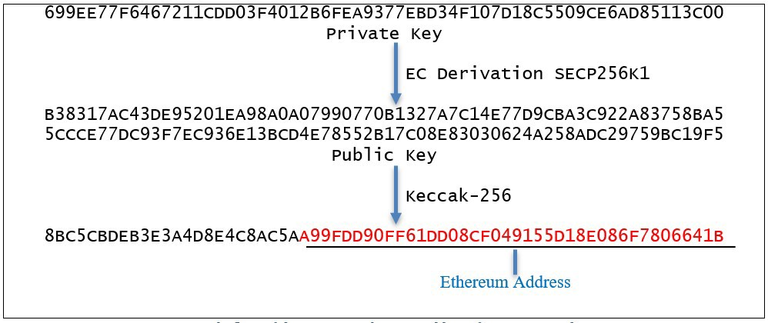
Amber explained that Profanity relied on a particular algorithm to generate large sets of public and private addresses that had certain desirable characters. The Profanity tool created millions of addresses per second and searched for the desired letters or digits that were requested by users as custom wallet addresses. Still, the process used to generate those addresses lacked randomness, and private keys could be reverse-calculated with GPUs.
Still we have so many critical facts that threat crypto deveopment and its stability.
As crypto sector develop more secured network and protocols experiencing many critical issues, overall security and stablility of crypto and digital assets would become stable and acceptable that may be enough level to accept public in this territory.
But as we face these accidents more and more, I acknowledge it would be extemly dangerous just depending on programmers and small group of developers who have very narrow view and insisit on their own way.
Crypto sector may need more chalenges and many developers and participants who are lack of mature mind set should be set back.