A Wifi network (Wireless Fidelity), consists of a connection environment, generally with Internet access that we can achieve through the use of electronic devices called routers.
Routers can convert the Internet signal that travels over the telephone network (wired or wireless, satellite) into low-frequency radio signals, generally, 2.4 GHz, which is the same frequency as many other household appliances such as the oven. microwave, cordless phones, etc.
A wifi network not only allows access to the internet but also the interconnection and transmission of data between the devices that make it up (tablets, phones, PCs, smart-tv's).
Security levels in Wifi networks
If you have had the opportunity to configure a router, surely you have noticed, in the security options, the initials WEP, WPA, WPA-2, SSID, WPS.
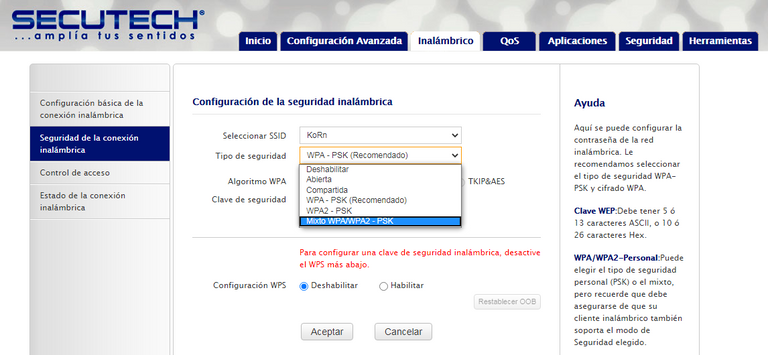
WEP (Wired Equivalent Privacy)
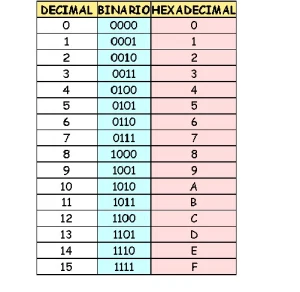
This was the first security standard and it is characterized because its keys or passwords are expressed in "hexadecimal", that is, they use the combination of a set of 16 alphanumeric characters that include: S = {1,2,3,4,5, 6,7,8,9, A, B, C, D, E, F}.
Source
This security standard was totally hacked and does not represent the minimum level of real security in Wi-Fi networks.

WPA and WPA2 (Wireless Protected Access)
Once the weaknesses of the WEP standard were revealed, a new one called WPA was created, which was also hacked later. It is much more difficult to violate this type of network because it deserves more complex processes but it was also defeated.
Then WPA2 is created. This is a much more secure protocol based on the 802.11 wireless security standard, almost impossible to hack, but with one exception: In 2017 they discovered an attack which was called "KRACK" (Key Reinstallation Attack) which consists of deceiving a member of the network, asking them again to enter the connection password.

SSID (Service Set Identifier)
It is the name of your wifi network.
There are some wifi networks that have no name. This option can be configured on the router as a security measure.
This security method adds some complexity to the hacking process since before the passwords are discovered they should first determine the name of the network. This type of method is called "security by darkness".

WPS (Wifi Protected Setup)
We could call it a "physical access" security method. Since it is implemented by pressing a "button" that the router has and that allows adding devices to the network just by entering an 8-digit PIN code.

Source
The weakness of this method is that someone can access the PIN code which is usually written at the bottom of the router.

MAC (Media Access Control)
Finally, there is a security method that consists in adding the MAC addresses of the devices that you want to add to the network in the router's access configuration.
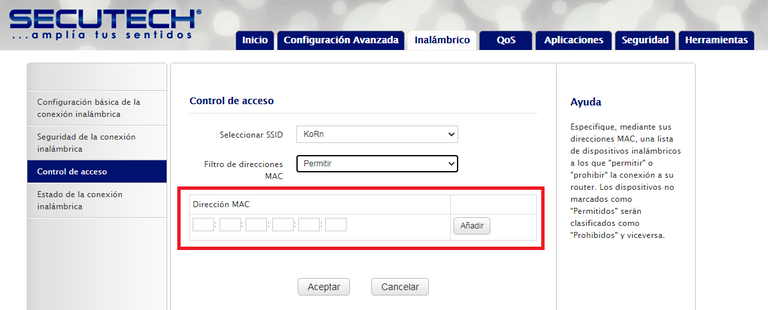
The MAC address consists of a unique global numeric alpha code (6 blocks of two hexadecimal characters (8 bits)) that functions as a fingerprint of electronic equipment, card, or network device.
This method is very safe, with the exception that if an attacker knows your device's MAC address, he could "clone" it using specialized software implementing a technique called MAC Adress Spoofing.

Conclusion
Each security method for Wi-Fi networks offers a certain level of protection which will vary from one to the other. As we could see, some methods are safer than others, but none of them gives us total security. So if we want to increase the protection level of our network we should implement a combination of all these methods. Although it seems exaggerated there are always people trying to access our data and our personal information, so in terms of privacy there will never be redundant methods.
@juanmolina


Vive la experiencia BraveBrowser. Navegue rápido y seguro mientras gana tokens BAT.
Por favor descargue el navegador Brave usando mi Enlace de Referencia.

I invite you to support @Yehey as a witness.
He is doing a great job for this blockchain.
You can get more information on how to support him here:
BLURT Witness Server is UP. Please vote @Yehey as one of your witness.
